From threat detection to rapid response, we protect your data and reputation with enterprise-grade tools tailored for small and growing teams.









We’re a focused cyber team helping growing companies harden their environments, detect threats early, and respond fast. No fluff—just clear security outcomes and predictable pricing.

We provide continuous protection across endpoints and networks with real-time monitoring, detection, and response. Our team maintains hardened baselines, proactive patching, phishing defense, and fast incident handling to keep your systems resilient.

Privacy is built into everything we do. Data is encrypted in transit and at rest, access is restricted by need, and retention is minimal. Our practices follow global privacy standards to ensure trust and transparency.
We provide end-to-end cybersecurity solutions that help organizations detect, prevent, and respond to threats with speed and precision.
From risk assessments to continuous monitoring, we ensure your business stays one step ahead.

Coming soon! We simulate real-world attacks across web apps, APIs and infrastructure to uncover exploitable paths. You get a clear risk rating and prioritized fixes.
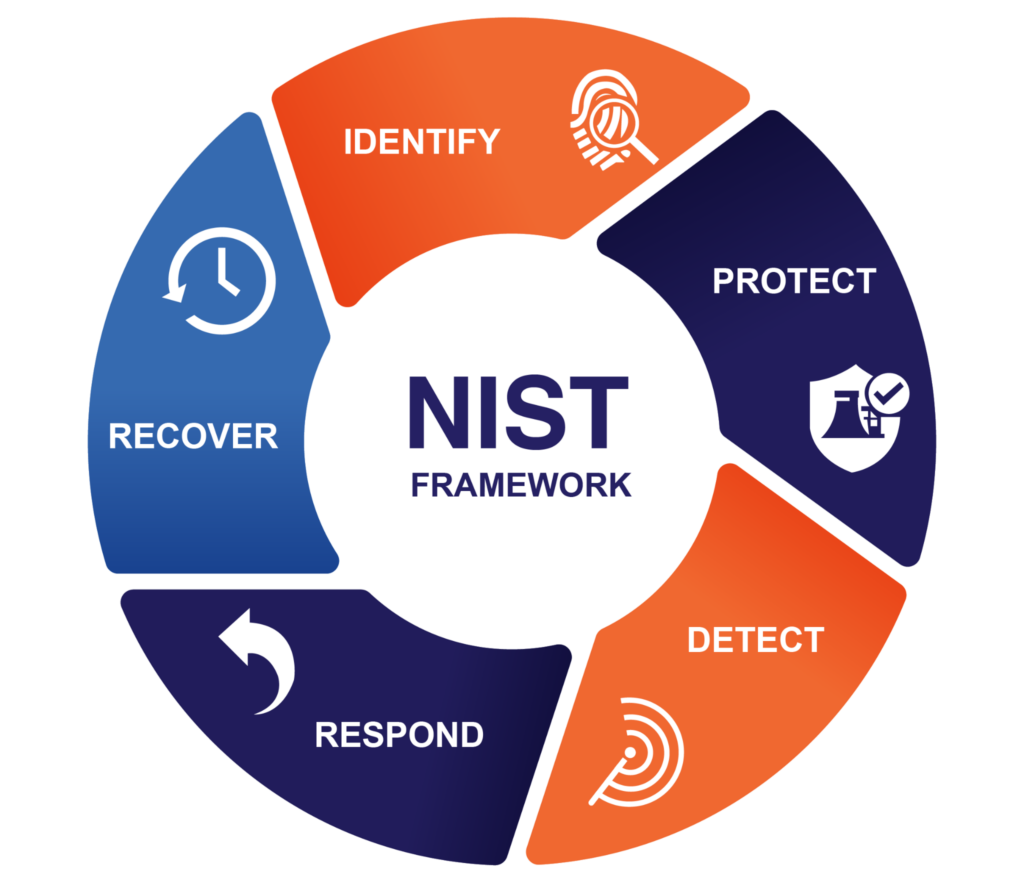
Automated and manual scans with a remediation plan. Establish a baseline and track deltas quarter-to-quarter.

Containment, investigation and recovery. Evidence capture, root cause analysis and lessons learned to prevent repeat incidents.

Continuous monitoring, alert triage, hardening and patch guidance with regular reporting — we act as your SOC.

Endpoint, server, and hardening with a clear patch cadence and EDR. We reduce attack surface and provide simple monthly health reports.

Phishing simulations and bite-size training tailored to your risks. Metrics show improvement over time.
We combine technology, expertise, and vigilance to deliver reliable, real-time protection.
With CyberWardion, your systems are monitored, hardened, and secured — always.

Comprehensive cybersecurity coverage designed to protect your business from every angle.

Real-time monitoring and quick response, ensuring uninterrupted protection.


Choose a plan and we’ll tailor it to your environment—Get Started takes you to our quote form.



Avoid clicking suspicious links or downloading unknown attachments.
Keep your browser and system updated.
Use a VPN when on public Wi-Fi.
Enable antivirus and endpoint protection software.
Use strong, unique passwords and enable multi-factor authentication wherever possible.
Our co-managed model allows your internal IT or security team to collaborate directly with our cybersecurity experts. We provide 24/7 monitoring and incident response support, threat detection and triage through our SOC platform, regular security reports, and actionable insights.
This partnership gives you full visibility and control, while we handle the complex security operations — ensuring your organization stays secure, compliant, and resilient.
Critical alerts: Immediate notification via email, dashboard, or SMS.
High/Medium alerts: Daily or real-time notifications depending on your SLA.
Low-severity alerts: Included in weekly or monthly summary reports.
All alerts include clear remediation steps and our analyst’s recommendations to help your team respond quickly and effectively.
We store data securely in encrypted environments, both at rest and in transit. Access is restricted using least-privilege principles and monitored continuously. Logs and customer data are retained according to compliance requirements (e.g., GDPR, ISO 27001) — typically between 60 days and 12 months, depending on your plan.
Your data is never shared or sold, and all backups are encrypted and stored in secure, access-controlled locations.
We combine enterprise-grade security operations with transparent communication and customizable solutions. Our clients benefit from advanced automation, real human expertise, and tailored cybersecurity strategies — without the complexity or cost of building a full internal SOC.
We’re your trusted partner in detection, response, and prevention — protecting your business so you can focus on growth.
Find out more about Cybersecurity.


CyberWardion is a cybersecurity company dedicated to protecting businesses from modern digital threats. Our mission is to help organizations strengthen their defenses, detect attacks early, and maintain full control over their data and systems.
© 2025 CyberWardion. Guarding your digital world. All rights reserved.